
Attackers cannot hide on the internet — they leave behind cyber fingerprints across internet infrastructure.
Prior to launching a campaign, attackers need to pay for, build, or borrow the infrastructure needed. For example, they set up servers, obtain or reuse IP addresses, and register domains to use. This often happens before they even perform reconnaissance on their targets or create the malicious payload. And all of this activity leaves fingerprints about the attack.
Cisco Umbrella Investigate provides the most complete view of the relationships and evolution of internet domain names, IP addresses, networks , and malware — helping to uncover the infrastructure being staged and hunt emergent threats. Here are just some of the items that the Umbrella can help uncover on your network.
Internet-wide visibility ☑️
Predictive intelligence ☑️
Pivot through attackers’ infrastructure ☑️
Investigate connects the dots between attackers’ infrastructure, which helps attribute domains to specific attacks and malicious activity. Our statistical models accurately identify malicious domains, IPs, ASNs, and file hashes across the internet, and even predict where future attacks maybe staged.
With Investigate, you can pivot on different data points to see how domains are related to IPs, ASNs, and malware to map out the infrastructure used in an attack and uncover future malicious origins. Cisco Umbrella Investigate provides global intelligence to help security teams hunt and identify threats before the kill chain begins. Let’s walk through an example of what you can uncover.

Other malicious domains registered by the same email address can be found by pivoting on the WHOIS record data. This uncovers other connected domains that can be further researched.
WHOIS record data uncovers details about who registered the domain, contact information used, when and where it was registered, and more. You can even find domain ownership changes with historical WHOIS data. Domain-to-ASN mapping enables you to pivot from domain to ASN and uncover other malicious domains on the same network.
Related domains and co-occurrences identify other domains that were queried with a high statistical frequency right before or after this one and could be part of the same attack. All domains hosted by the IP shows all domains, including malicious domains, hosted by this IP. Even if some of the domains are not bad now, they’re considered suspicious due to their associations.
Your need: always-on network security
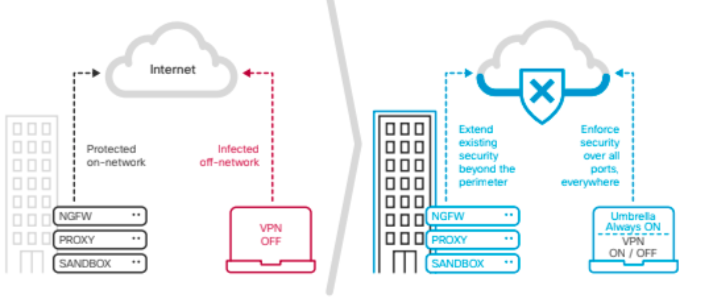
It’s quite simple: the more your associates and partners collaborate with clients, the faster the firm grows. But access to your client’s data makes your firm a prime target for attacks, so you’ve implemented a security stack with best-practices. You’ve stacked multiple security solutions (e.g. firewall, proxy, antivirus) for “defense-in-depth”. And yet, you’re still re- imaging laptops and flooded by security alerts.
Starting from a single domain, you’re able to use Investigate to uncover many more malicious domains and IPs that are connected to the same attacker infrastructure and can be proactively blocked. Need help with this? Next I.T.has you covered.

